Two weeks ago, at Microsoft Ignite in Orlando, Microsoft announced the public preview of Password-less phone sign-in. We enabled this feature right after the session in our company tenant, and we have all been super excited about this cool way of signing in. One big step closer to a more secure and password less world.
This blog post will explain how to configure password-less phone sign-in and how to enable this feature for your users. Please note that this is still a pre-release feature.
Prepare the Tenant
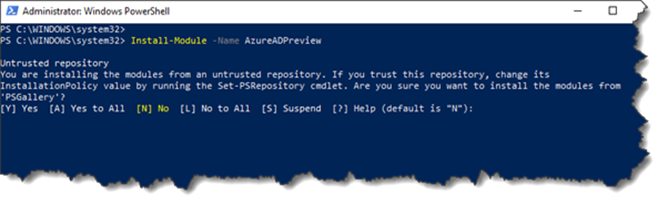
First we need to install the latest version the of Azure Active Directory V2 Preview PowerShell Module. This can be done by running the following PowerShell command:
Install-Module -Name AzureADPreview
Please note that the AzureAD Preview Module might need to be updated, if your already have an older version installed.
When the Azure AD Preview Module is up to date, you can connect to your Azure AD, with the following command.
Connect-AzureAD
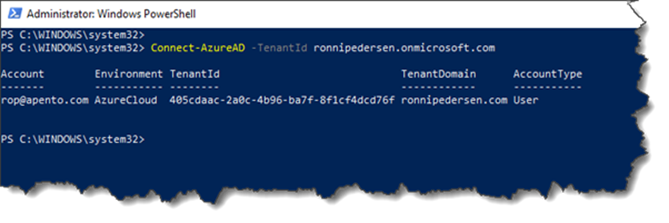
If you are connecting to a customer tenant and want to enable this with your own B2B account, you need to specify the TenantId and you must be either Security Administrator or Global Administrator.
Connect-AzureAD -TenantId ronnipedersen.onmicrosoft.com
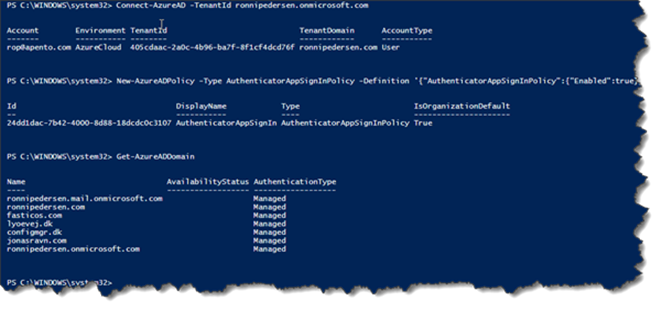
When connected to the tenant you need to configure, you just need to run the following command:
New-AzureADPolicy -Type AuthenticatorAppSignInPolicy -Definition ‘{“AuthenticatorAppSignInPolicy”:{“Enabled”:true}}’ -isOrganizationDefault $true -DisplayName AuthenticatorAppSignIn
That’s it… You have now enabled phone sign-in for all users in the Tenant.
Enable phone sign-in for users
For the public preview, there is no way (that I know of) to enforce users to create or use this new credential.
End users will only encounter password-less sign-in once the user has updated their Microsoft Authenticator App to enable phone sign-in.
Important: This capability has been in the app since March of 2017, so there is a possibility that when the policy is enabled for a tenant, users may encounter this flow immediately. Be aware and prepare your users for this change.
Pre-requirements
- Enroll Azure Multi-Factor Authentication.
- User the latest version of Microsoft Authenticator for iOS 8.0 or Android.
More information on how to get started with the Microsoft Authenticator app:
https://docs.microsoft.com/en-us/azure/active-directory/user-help/microsoft-authenticator-app-how-to
When the Microsoft Authenticator App is configured and working as expected, users must perform the following steps to enable Password-Less Phone sign-in:
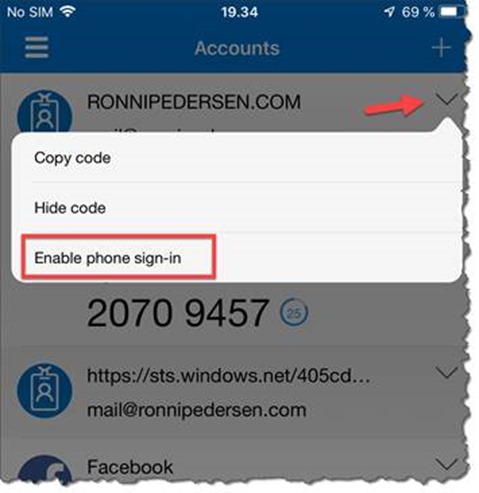
Go to the Accounts screen of the app, select the drop-down arrow for your work or school account, and then select Enable phone sign-in.
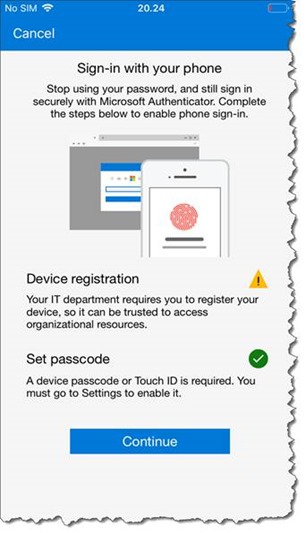
One of the prerequisites, is that the device is registered within the Azure AD tenant, to an individual user. Due to device registration restrictions, a device can only be registered in a single tenant. Basically, this means that only one work or school account in the Microsoft Authenticator app can be enabled for phone sign-in.
Click Continue to register the device.
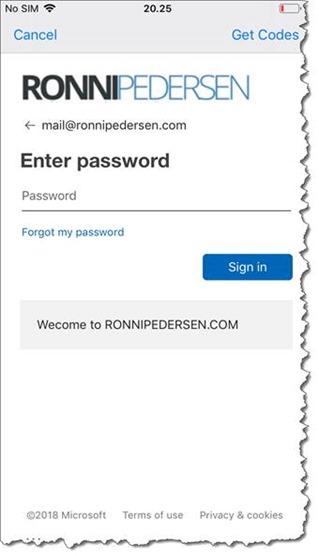
You will get prompted to sign-in…
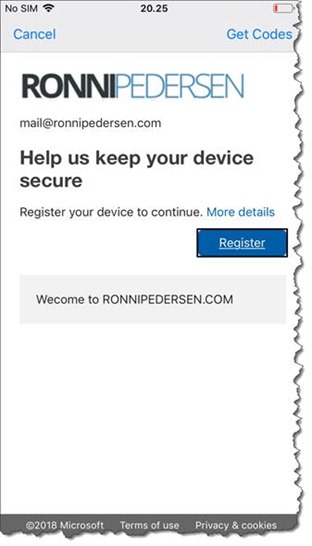
And then you will get prompted to register the device.
When the device registration process is complete, you are ready to sign-in without using a password.
End User Experience
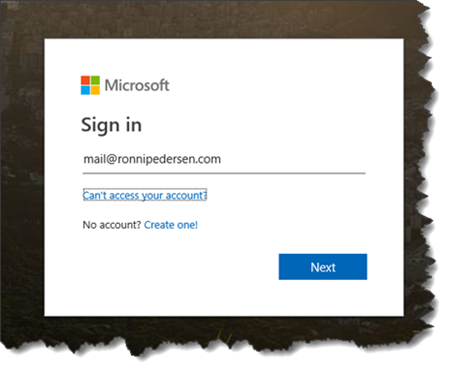
To test this just sign in to your work or school account, as normal (If required use a private browser).
Type your username and click Next.
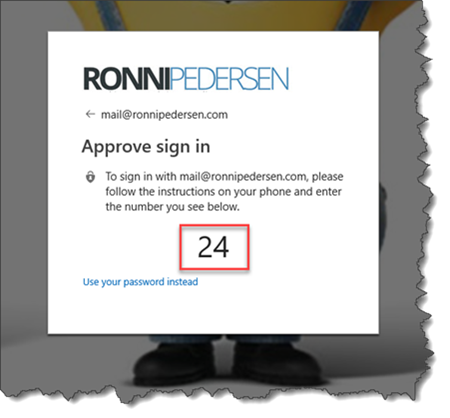
You should then see a page with a two-digit number, asking you to approve the sign-in through the Microsoft Authenticator app. If you don’t want to use this sign in method, you can always select “Use your password instead”.
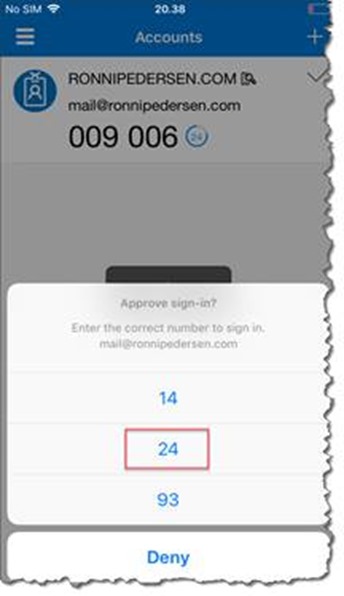
In the Microsoft Authentication app, you’ll get a notification asking you to Approve sign-in.
Tap the same number you see on the Approve sign-in screen. Use your phone’s PIN or your biometric key to complete the authentication.
That’s it… You are now one step closer to a more secure and password-less world!
Learn More
If you want to learn more about Getting to world without password, you can see the full session from Microsoft Ignite 2018 right here:
Download the Slide Deck:
https://mediusprodstatic.studios.ms/presentations/Ignite2018/BRK3031.pptx
/Enjoy


10 Comments
Pingback: Azure Weekly: October 15, 2018 – Build Azure
Hi Ronni
Do you have any experience in how we can handle having multiple accounts in the authenticator? I set it up on one of my accounts and now I can’t set it up on the rest because it says my device is registred with another organisation? It is actually the same organisation, but different domains on the same tenant.
Regards Casper
Hi Casper,
One of the prerequisites, is that the device is registered within the Azure AD tenant, to an “individual user”. Due to device registration restrictions, a device can only be registered in a single tenant. Basically, this means that only one work or school account in the Microsoft Authenticator app can be enabled for phone sign-in.
This might change in the future, but for now you can only add one account.
/Ronni
Hi Ronni,
Thanks a lot for this article.
I configured the phone sign-in in my tenant and my authenticator app but it only wotks the first time I log in, I have to type my password if I reboot or lock my laptop. I completely disabled Hello for Business, just in case, but it still doesn’t work.
Is there any step I’m missing?
No sure what can cause this. It works perfect for me…
I tried to follow you guide above however i am running into an error enabling the policy.
New-AzureADPolicy : Error occurred while executing NewPolicy
Code: Request_BadRequest
Message: Property has an invalid value.
InnerError:
RequestId: 3df40991-b3a8-4823-b414-6324bfb0fc3c
DateTimeStamp: Fri, 26 Oct 2018 03:33:06 GMT
HttpStatusCode: BadRequest
HttpStatusDescription: Bad Request
HttpResponseStatus: Completed
At line:1 char:1
+ New-AzureADPolicy -Type AuthenticatorAppSignInPolicy -Definition ‘{“A …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [New-AzureADPolicy], ApiException
+ FullyQualifiedErrorId : Microsoft.Open.MSGraphBeta.Client.ApiException,Microsoft.Open.MSGraphBeta.PowerShell.New
Policy
Any thoughts why I cant enable it? i’m logged in as global administrator btw, Thank you
No. Try to contact MS support.
Spencer,
The reason that you get the error is that if you copy and paste the command from the website the single and double quotes are interpreted wrongly. You need to replace with ‘ and ” respectively.
Ronni,
Set this up and works as expected however I set up a conditional access rule for Exchange Online only and excluded trusted locations. It doesn’t appear to obey any of the conditions specified and applies to all web apps from all locations.
Did you have the same experience ?
I haven’t used trusted locations with this feature yet… I’m not a big fan of trusted locations.
Pingback: enable phone sign in authenticator – datahowinfo